It has finally happened: policy based routing is available for the Cisco ASA platform. This comes about from the new version 9.4 of the ASA software. While a lot of the time policy based routing is done on the routers themselves, there are definitely uses for having is on your ASA firewall such as in the cases of multihomed connections, etc.
- Cisco Asa Policy Based Routing
- Asa And Policy Based Routing
- Asa Firewall Policy Based Routing
- Policy Based Routing Linux
- Asa Policy Based Routing Nat
ASA Policy Based Routing This post describes how to configure a Cisco ASA firewall to support Policy Based Routing (PBR). PBR allows an administrator to define routing based on source address, source port, destination address, destination port, protocol or a combination of all these. Policy Based Routing Feature in ASA No, there is still no PBR as of ASA software 9.1 (4) (= the latest as of this posting). I have not heard of it being added to upcoming releases. We steer customers with ASAs and PBR needs to use upstream routers with the full set of IOS features available on them.
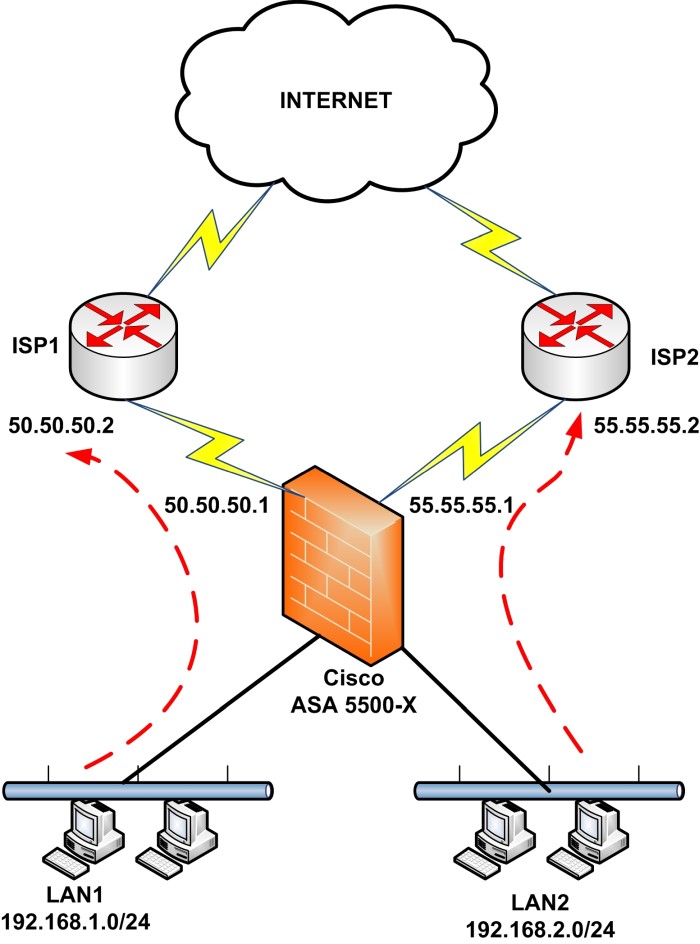
For those unfamiliar with policy based routing, basically is allows a user to match specific traffic that is designated with an access list accordingly and then set specific actions or specifications for that traffic. The most common that you will see is the next-hop IP. For users dealing with multiple ISP's, they can now specify which ISP is used based on things like which source the traffic is coming from. This was something that was not possible before this update. There is a catch though as there always is with new things. This update will only be available for the newer, X series firewalls like the 5545-X. Unfortunately that old 5505 and 5510 that are hanging around will not have this update released for then anytime soon.
If you are looking at configuring this on your ASA running 9.4, here's an example on how to get started straight from Cisco's site:
Examples for Route Map Configuration
Cisco Asa Policy Based Routing
In the following example, since no action and sequence is specified, an implicit action of permit and a sequence number of 10 is assumed:
In the following example, since no match criteria is specified, an implicit match ‘any' is assumed.:
In this example, all traffic matching will be policy routed and forwarded through outside interface.
In this example, since there are no interface or next-hop actions are configured, all traffic matching will have df bit and dscp fields modified as per configuration and are forwarding using normal routing
Sheba Prokashoni (Bengali: সেবা প্রকাশনী) is a well-known publishing house in Dhaka, Bangladesh. It was founded by Qazi Anwar Hussain. Sheba's books have enjoyed great popularity among young Bangladeshi readers, and it is particularly notable for its accessible translations of Western literary classics into the Bengali language. Sheba western pdf free. Bangla PDF books of Sheba Prokashoni Books. Bengali pdf ebook download. All books of Sheba Prokashoni Books download in PDF file. Collection of pdf Bangla ebook. Bangla books of Sheba Prokashoni Books. Free download Sheba Prokashoni Books's book or read online. Free bangla book download, bangla book download, bangla book pdf, bangla book, bangla islamic book, study tips, educational degrees,MBA, BBA, university, bangla novel, kobita, golpo,free ebook downlod, humayun ahmed book download, bangla boi download. All Western Books From Sheba Prokashoni ডাউনলোড করুন.
KB ID 0001042
Problem
I've been working on a large firewall deployment for a client, each of their DMZ's have both a production and a management network. nothing particularly strange about that, but each of their DMZ's has its own firewalled management network and it's routable from the LAN.
So If I'm an admin and I want to talk to a Linux appliance in their DMZ via its management interface, my traffic leaves the LAN through the management firewall, but the appliance sees my source IP as being on the LAN, and routes the traffic back to me via the clients production firewall.
Now the simplest way to fix it would be to put a static route on the appliance to route my traffic back via the management firewall, which is fine, BUT what if that appliance is the proxy server? Now I can administer it, but I cant get on the Internet!
Note: I'm NOT performing NAT anywhere in this scenario!
Solution
Well I could simply PAT the network my laptop is on, lets say its 172.16.1.0/16 to the DMZ interface of the management firewall.
The problem with that is it will translate all traffic from my laptop's subnet going into this DMZ and I might not want to do that.
Asa And Policy Based Routing
Solution Pre ASA 8.3
We used to have a really simple way of solving this problem, ‘policy based nat', you specify a set of conditions with an ACL then anything that meets that ACL is tied to a specific NAT rule.
Asa Firewall Policy Based Routing
Solution Post 8.3
To do the same now the syntax is a little different. To demonstrate I have built a small lab in GNS3 to demonstrate. If I want the internal host to talk to the DMZ host, I want the traffic when it gets there to ‘appear' to have come from 192.168.131.1
To demonstrate, if I ‘ping' the DMZ router from the Host router, and Wireshark the traffic when it gets there, I see its coming from its actual IP address.
To NAT this traffic use the following commands;
Policy Based Routing Linux
Now if we repeat the process, and ping the DMZ host.
Now when I capture the traffic, the source IP has changed accordingly.
Asa Policy Based Routing Nat
Related Articles, References, Credits, or External Links
NA

